1
I'm seeking help about some impossible to track down malware spamming all my contacts list using direct SMTP sending.
It uses my personal email address (ISP, POP3/SMTP based, NOT web based, as I could find nothing but gmail or hotmail related problems and answer on the web, which is NOT my case) and is able to browse and use my contacts list to send short spam mesasges with a link to some infected website to a group of recipent (the only way to detect something wrong is going on is receiving failure return messages when one of the addresses in the list is obsolete, for instance, or when one of the recipients' server or ISP server rejects it)
My ISP has checked the history from the dates and times indicated in such returning warnings, and is able to certify the spam was actually sent from my IP address, so it's NOT only spoofing my address : my computer was the actual sender. BTW, all the recipients are in my actual contacts list.
It started when I was using my old computer running Windows XP and using Outlook Express. However, it now does the same on my brand new computer running Windows 7 Pro and Thunderbird, meaning it's also able to browse my Thunderbird contacts list, and not just the old Outlook Express obvious WAB file.
Recently, one of my customers has now reported the same problem (they've noticed when some of their customers servers have blacklisted them and they're started to receive the same undelivered return messages as I've been experiencing). BTW, their ISP is the same as mine (see below about the fact they may still allow anonymous SMTP). In her case, her computer is running Windows 10 Professional and she's using MS Outlook 2007.
- It most probably doesn't use my email client program to issue the spam emails anyway (though of course it's hard to say if it doesn't launch it in the background), but though the computer has of course to be left turned on, it usually sends them at night (most of the time around 1 to 3 AM, though sometimes they were issued during day time) when my email client is closed.
So it has to directly connects to my ISP server with SMTP (using of course my email address and password, though my ISP might still allow anonymous SMTP, wich is of course a problem).
Unfortunately, my local ISP doesn't use SSL nor TLS encryption (though I guess it wouldn't change much as long as no password is required). However, considering it could get my email address and contacts list, I guess it was probably not that hard to get my stored password as well, since NirSoft is able to do so, for instance).
- No antivirus software could detect anything, yet it's still there, spamming my whole contacts list about twice a month, sometimes more often, sometimes only once : the frequency, hour, etc. are totally random and unpredictable.
I've tried all that was advised on the web with absolutely no result at all.
- Of course, manually checking the registry, services, etc. shows nothing suspect at startup. And yet, the damn process has to be lurking somewhere, or it wouldn't be able to burst hundredths of emails within a few seconds like it does !
So now I've just tried to block it using firewall rules ;
However, using the Microsoft firewall, I could add an outgoing rule allowing Thunderbird to use port 25 with user authentification, but I'm totally unsure if this makes the rule exclusive, i.e. enabling this probably doesn't disable any other use.
Unfortunately, adding another rule blocking port 25 doesn't make the above rule an exception. If I do so, it just prevents me from sending any email at all, despite the explicit permission. Apparently, the prohibition rule overrides the permission one, where I'd like to get the exact opposite behavior (block all, then allow the exception).
Ideally, I'd wish to get any attempt out of the only allowed app (Thunderbird in my current case) to be logged so I could track down the culprit.
Has any of you ever heard of such a problem, and maybe could lead me to a solution, or to someone able to solve this problem, or would know of any tool that would be more efficient at detecting it ?
Does anybody know how I could setup the firewall so it blocks any use of port 25 but from one allowed app ? And ideally, how to log any attempt from any process but the allowed one ? Or maybe some free third party firewall software that would do the job ?
Of course, identifying the culprit and being able to eliminate it would be perfect, but if it can't be done, preventing it from harming would still be an acceptable compromise until antiviruses would be able to detect it one day.
EDIT :
Here's a sample : http://www.mediafire.com/download/relstor86wkfw44/Undelivered_Mail_Returned_to_Sender.eml.zip
EDIT : so in conclusion, analysing the header will help you know if the spam was originated from your PC or if your email address has been spoofed.
Problem solved in my case, thanks to David's answer below. This explains why no antivirus tool could find anything suspect in situ.
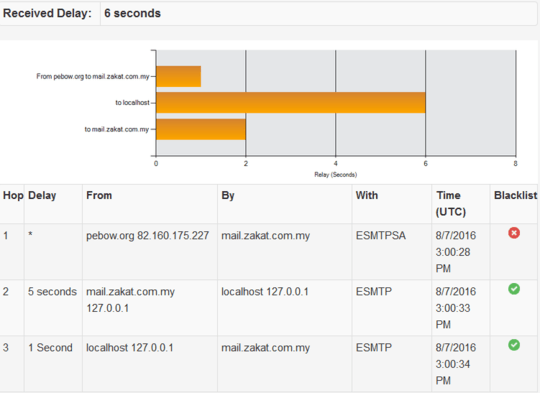
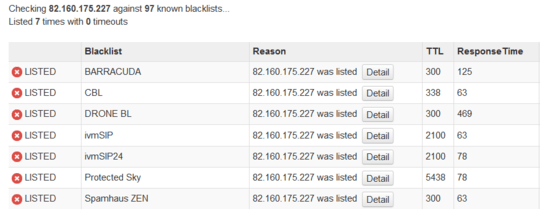
1This isn't a forum, its a Q&A format, and works differently. What's the exact error? Maybe something you're saying is tripping the spam filter, and/or you have some new user wierdness. Extending a question into an answer is not how we do things here – Journeyman Geek – 2016-08-31T11:50:35.817
1It's a bit strange complaining about not enough space when you use paragraphs like "My ISP.... contacts list", where you just could have written: My ISP verified the spam came from my IP – Jan Doggen – 2016-08-31T11:52:20.137
merged the contents of the 'answer' into the question. Feel free to edit as needed – Journeyman Geek – 2016-08-31T11:53:11.087
OK, thanks to have managed to group my post. I hope someone would have a hint, as It's been annoying me for over 6 months and some other epopel are starting to experience the same problem on recently setup computers, different Windows versions and different email clients... – Z80 – 2016-08-31T11:55:15.727
Who is your ISP? – DavidPostill – 2016-08-31T11:56:25.800
No, nobody is tripping with any spam filter. My ISP has one that works only on reception. else I'm using a standard Thunderbird setup with POP3/SMTP settings. We do have our own email server for the company, but only my personal (ISP related) address is concerned. Smilarly, only one address (one of the managers') seems to be concerd at my customer's, suggesting the problem is localized to a specific PC. – Z80 – 2016-08-31T11:57:24.510
1>
"Unfortunately, my local ISP doesn't use SSL nor TLS encryption (though I guess it wouldn't change much as long as no password is required)" If your ISP doesn't require a password anything is possible. – DavidPostill – 2016-08-31T12:02:27.970
I have read your question three times. I still don't understand what your actual problem is, nor do I know, what your asking us. This is an example of an over complicated statement, if your ISP does not support SSL don't even mention it, not supporting SSL isn't the reason for your problem. – Ramhound – 2016-08-31T12:02:34.813
Why ? First of all, i'm not anymore, but reasons were multiple (Jeez, as you say, that's lucky it's only comments, it would be weird it was in the messages), starting with : "what's not broken you don't have to replace", then "I'm using various 16 bits apps, starting with management software in Clipper 87, plus other specific ones". Then specifically about Windows 10, I've updated it on my home PC after having stupidly installed Windows 7 in 64 bits. As a result, MS has now removed XP Mode and I can't use Graphic Works 4 anymore at home. – Z80 – 2016-08-31T12:03:47.840
@Z80 - You could. VirtualBox, VMWare, Hyper-V (Windows 10 Professional) all could allow you to run a Windows XP virtual box and run that program. In the case of VMWare and Hyper-V I believe both support a unity mode which would allow it to run virtually seamlessly. – Ramhound – 2016-08-31T12:05:30.267
@ Ramhound1 > something on my computer, and other people's, is spamming emails addresses to their whole address book a few times per month, and no virus detection tool is able to find anything. The question is : do you know any mean do find it ? – Z80 – 2016-08-31T12:05:36.917
Yes, about 16 bits apps, i'll probably end up using VMWare for the few apps I'm still needing. At work, I'll just stick to Windows 32 bits. Anyway, that's not the question here.The virus is not related to this. I just mentionned the fact it apparently managed to transfer to another computer using a different OS, though it might as well have entered later, who knows. And yes of course, all my stuff had been checked for viruses by various means, and nothing has ever been found. That's actually the main problem : it's totally unseen but still there. – Z80 – 2016-08-31T12:08:51.803
Just to make things clear : my Windows XP was the last of a very long chain of updates starting with MS-DOS 4 through all the computers I had from the start. However, my current one has been installed from scratch, then I copied the files (with of course a running antivirus). However, to get the emails, I had to install Thunderbird on the old computer so it auto imported them, then I copied the folder to the new computer. Maybe that's how it passed from the old one to the new one... Anyway, the virus acts without Thunderbird launched, and I'd like to track it down, if possible. – Z80 – 2016-08-31T12:11:42.180
Of course I'm aware the ISP accepting anonymous SMTP sending is a serious glitch. The strange thing is it's supposed not to work anymore, and this has been done years ago, after a serious spam outburst having led to their whole domain bein blacklisted by various international IPSs. But the fact I can sometimes still find some old setups without password authentifications to work when stumbling on them on customers computers proves they apparently still have it working? Actually, they have 2 servers : mail.canl.nc (accepting anonymous login) and pop.canl.nc (password required), both on port 25. – Z80 – 2016-08-31T12:15:55.273
The "mail." one should not work anymore, but it apparently still does, since I sometimes find it on some old setups, and users don't seem to have any problems sending emails ! But AFAIK, I know the ISP would block them if they would issue spam; I just never happened to them. I could suggest them they completely remove it (it should have been done anyway), but it would give results only if the virus would use anonymous login... It's a possibility, but not a certainty. The sent emails are enclosed in the returning error messages, do you think they could contain any information about this ? – Z80 – 2016-08-31T12:20:02.647
"do you think they could contain any information about this" If you can [edit] the question to include the full mail headers of one of these spam emails we might be able to tell something about them. – DavidPostill – 2016-08-31T22:23:16.370
Hello David, thanks for caring. I've edited the people's actual addresses in the text for privacy concerns and renamed the .eml into .txt for safety. Thanks for helping, though I doubt there's a hint about the sender process in it. I've joined both the return email and its attachment, though it's probably included in the email as well. – Z80 – 2016-09-01T14:50:35.760
Your ISP is incompetent. Email didn't come from you. You are getting backscatter from spam forged with your email in the return path. See my answer for a full analysis and explanation. – DavidPostill – 2016-09-01T20:41:04.670
Hello David, that would be a possibilty ; however, how comes all the addresses in the recipients list are actually all in my address book ? It would be an impossible coincidence IMHO. – Z80 – 2016-09-05T01:13:07.703