123
28
Why does anti-virus software not completely delete the viruses, malware, etc., but instead quarantine them? Is it not better to completely get rid of them? Why? And how can I manually remove them?
123
28
Why does anti-virus software not completely delete the viruses, malware, etc., but instead quarantine them? Is it not better to completely get rid of them? Why? And how can I manually remove them?
135
Viruses and malwares are not dangerous if not executed.
A file in quarantine cannot be executed by the user and the malicious code (virus or malware) has no possibility to act. If the virus/malware is removable it will be removed immediately.
If not the file will be moved to quarantine.
There are different reasons for this:
Possibility to study the virus by the antivirus company or to individuate other computer with the infection (let's imagine you have a file attacked by a virus. Its signature, md5sum changes. You have the same file on many computers. If the signature is the same you can guess they are attacked. If you check in your backups you can find the first time the virus acted).
Note: historically the "quarantena" was a period of 40 days isolation for ships and people before entering the city in order to prevent the diffusion of the Black Death, to see if the virus develops or not. On our computers the quarantine is just a safe place were to keep inactive the suspect files, without observing any actions of the virus.
In the quarantine can end up even an executable file that is changed.
Imagine that you have a program that you recompile or an open source program that is updated not via usual windows ways: the antivirus can notice activities (writing) on an exe-cutable file and put it in quarantine.
Moreover since there are some files with active content (as, e.g., Word or eXcel macro...) some antivirus can spot differences in the executable parts and interpret those as produced by the action of a virus.
If you have the same version of a file attacked from a virus in different ways, it can be (theoretically) possible to recover the file by crossing and analysing data of these versions.
Further explanation
Think like a virus and an antivirus to understand why the quarantine exists, why there can be false positives and why this is a battle that continues each day.
A virus (or a malware) is a compiled code that executes the purpose for what was programmed for.
As compiled code, it's binary (usually) and not text (as what you are reading). It has to propagate itself and to execute some homework (a mission, technically a payload), not necessarily at the same time (this increases the possibility of spreading the infection before it is detected).
How can a virus propagate itself and be executed?
Simply it can overwrite a part of the original code (exe,dll,com... files) and put its code instead.
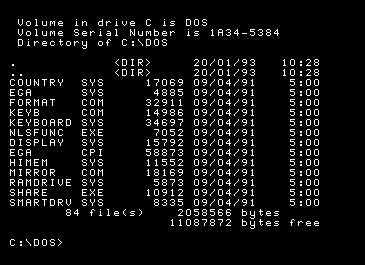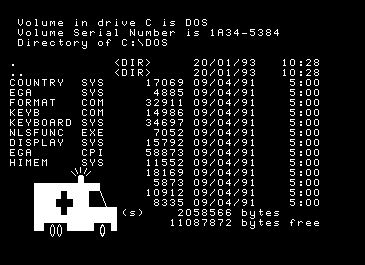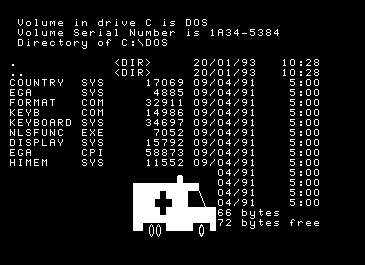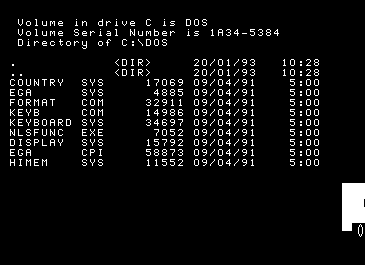
Example of an ancient DOS virus that acts in a such mode.
The drawback is that the original program can stop working and the virus may be detected faster (E.g.: "...hello my program is not working... strange things are happening... can you help? - Yes sir you have a virus").
It can copy the initial part of file to be infected at its end, after it can put itself instead of the first part. So when you execute the program, the virus is firstly executed and only then the program is executed... A smarter variant is to copy itself at the end of the file and to put a jump to the end in the beginning of the file (and one back to its beginning at its end)... The drawback is that an antivirus can search for the code of the virus (once known) and find it easily. This happened in the Cascade virus in the 80s-90s...
It can be made of parts and he (note not it) can change his shape and hide himself in different parts of the program, move them, encrypt and scramble. Each time he may infect a new file in a different way. Therefore the antivirus may only find remains in fingerprints – each day he is harder to identify.
Now, do you remember that the virus is (usually) binary code? Well, the fingerprints are too.
Since they are not the full virus but only a few bytes, it may happen that a part of a compressed file, data file, or image has the same bytes of one of the many known viruses fingerprints – hence the false positive.
Conclusive note: not all the viruses were planned to damage, but most of them do it, de facto.
With the actual use of computers with bank accounts and bills to pay, it doesn't seem any more as funny as the images above.
4+1 on this specifically because of future possibility to recover the file - once upon a time this was a standard course of operation for antivirus software! – fluffy – 2016-07-04T07:55:49.480
"an homework" - It looks like auto-correct got you there. But I can't guess which word you really meant. A common word would be payload but I don't expect that to be auto-corrected into homework. – MSalters – 2016-07-04T08:13:31.140
3@MSalters. Nope, sadly no auto-correction. I was speaking figuratively (or at least I was trying to): a virus propagates from a file to another (maybe another computer...). Then it resides in a file (it finds home). Then it waits... then it executes what it was taught for (programmed for). From here the term "homework" You can read it as "mission", it should be more clear, but it is more like if you see a virus as a soldier. BTW thanks for the spot, answer updated. – Hastur – 2016-07-04T08:39:45.513
2@Hastur: It might be useful to indicate which terms you came up with yourself, and which terms are standard. Your explanation confirms that you are indeed talking about the payload. See also Wikipedia: ", not all viruses carry a destructive payload.. Virus parts: Infection mechanism, trigger, payload". – MSalters – 2016-07-04T10:46:06.420
2
@MSalters ...and for this you downvoted the answer !?! I'm not speaking for a technical audience (that probably just knows the reasons for a quarantine). For this same reason I've not used the EB 7F or JMP SHORT to say that the virus jumps from a location to another. I chose to use a figurative speaking instead, without a word that in many dictionaries is not even reported with that meaning[ M.Webster L.,Collins ]... enthusiast ! --> technical, not always at least.
Ahh yes, 1990, truly "Ancient" times... – Ƭᴇcʜιᴇ007 – 2016-07-04T13:38:02.440
@Hastur Better than the 386 SX-16 (for "sux") I upgraded my 8088 to. ;) – Ƭᴇcʜιᴇ007 – 2016-07-04T13:50:25.380
@Ƭᴇcʜιᴇ007 OT Updated "Don't say to me": Ti994/a... ;) truly Ancient :D ... and I get The Cascade... (cool). Parsec forever !!!! look here
– Hastur – 2016-07-04T13:52:29.57741I'm curious about the "he (note not it)" portion. What was that about? – Alpha – 2016-07-04T18:20:56.010
3In the phrase "In the quarantine even an executable can be finished", I can't figure out what the word "finished" means. Can you clarify this? – Tanner Swett – 2016-07-04T20:27:38.983
4@Alpha (and others...) It's personal, related to the way I "sense" that kind of viruses. The formers executed basic tasks,blindly,with no exhibit of any kind of brilliance. But then they started to modify themselves,to hide and remain sleeper, encrypting themselves,somehow evolving... --the variants easy to be found had no possibilities to survive resisting to your attempts to kill them; look: I used "survive" &"kill", implicitly I start to recognise them some sort of dignity as expression of Intelligence, as if they were alive... so not any more it but he,or she if you prefer. – Hastur – 2016-07-05T08:24:28.793
3...but to distinguish between he and she means to give them even a character, and for the moment it seems too much for my figurative speaking too, even if I have to admit that some of them seems to behave like an he and some other more like a she. :-) – Hastur – 2016-07-05T08:55:57.543
@TannerSwett I suppose I forgot "up"; finish up in the meaning of end up. In an earlier version it was "In the quarantine can finish even an executable file that is changed.". After an edit I miss this rollback. Thanks. I'm going to update it. – Hastur – 2016-07-05T09:04:59.603
1"Viruses and malwares are not dangerous if not executed". This is misleading, I believe. More accurately, they would be not dangerous if they were never executed, past or future. Is it dangerous for a person to spread a virus even though it's never been executed? It certainly is. Is it viable/reasonable to ever assume that a virus that exists can never be executed? No it is not. A virus that does not exist is safer than one that exists, because there is always a non-zero chance it may be executed at some point in time. – Brad Thomas – 2016-07-05T19:33:12.627
@BradThomas tldr:if a virus(or intruder) has access to the quarantine database and files, it means that he has access to all your system and has no need to use the quarantined files. Note that it can find this Pandora's box even empty. Indeed to avoid such exploit, the antiviruses use fingerprints instead of the whole virus codes. If you're speaking of a human material error/deliberate action (Unix speaking kill -9 1 or rm -f / now patched but once definitive), well once again there is no need to search for and use the closed files in the quarantine zone. (it continues...) – Hastur – 2016-07-06T11:17:07.090
Time&Probability. Take an original DOS virus: today it cannot be executed under windows or Linux. Dosbox probably will stop it too.Technology advancements force expiring limits on the virus lifespan. I believe that an original idea appears because its time is arrived: in some time it can independently appear elsewhere making unnecessary the virus (and its creator) destruction. Instead if you learn how to defeat it, you will be able to contrast even the new ones. Imagine a boy, hit by a virus, that looses all the data from his preferred game. When grown he will be used to safe backup the data. – Hastur – 2016-07-06T11:31:03.363
1"Viruses and malwares are not dangerous if not executed" this is demonstrably false. Malware can exist in the form of a maliciously crafted payload in an otherwise benign file (such as Windows/GDI's JPEG execution vulnerability). What matters is how the file is quarrantined - if a naive AV were to simply move a bad JPEG file to another folder on the disk or perhaps put it in a zip file then there's nothing stopping Windows or another program from reading the file and triggering the bug. – Dai – 2016-07-07T04:31:13.837
1@Dai Yes, but that's still execution. Nobody is talking about double-clicking the file, just execution of the virus code. If there's nothing executing the code, there's no way for the virus to work (that's why we call it a virus in the first place, in analogy with biological viruses). – Luaan – 2016-07-07T15:34:25.810
1@TuringTux install sl. ;-) – Hastur – 2016-07-08T20:44:19.927
Consider amending this accepted answer to also include the fact that some people collect virus samples for various reasons. I personally keep a couple of CodeRed strains on my system in isolation and in a VERY benign format. I also keep the official EICAR test samples around for kicks. Obviously, I have to tell all AV packages to not scan certain directories because they love to quarantine those files. If an AV package outright deleted them, I would be extremely unhappy because that's data destruction. – CubicleSoft – 2016-07-10T14:23:11.633
Consider amending this accepted answer to also include the fact that there are several virus/malware sample trading communities out there. People collect and then trade virus samples. "I've got such-and-such a malware strain and want such-and-such a malware strain." Some people collect coins, baseball cards, etc. Other people collect computer virus/malware samples. In fact, many of the AV vendors built huge portions of their databases with samples from these communities. Deleting instead of quarantining would seed ill-will and distrust among the members. – CubicleSoft – 2016-07-10T14:30:02.037
88
Anti-malware applications provide a quarantine option, which is often on by default in order for two reasons:
39Additionally if the malware has embedded itself in a file you actually want, such as a Word document or similar, then outright deletion may be the worst option from the users perspective. Quarantine at least gives you a chance, however risky, to get the contents back. – Mokubai – 2016-07-03T08:03:28.520
8Additionally the anti-malware software might have a different understanding then you in the classification. Some anti-virus software are known to detect SysAdmin tools as malware and I found some of them deleting half my USB-Stick without asking when I connect it to computers from certain companies and schools. netcat, wireshark, etc. are known canditates. I have also seen people storing their only copy of their master thesis on an USB-Stick. I hope the anti-malware scanner doesn't detect it as false positive and deletes it without asking. – H. Idden – 2016-07-03T14:56:48.220
13Not very common? I think almost all detections my antivirus has had were false positives. – Oriol – 2016-07-03T17:49:27.663
1@Oriol: That could indicate the you may want to look at another antivirus, but the mais reason to chose one is its ability to block new threats and to fix the ones that did get through. The choice is a balance between the two. You can't test an antivirus by being careful, because being careful reduces the need for the antivirus. – Julie Pelletier – 2016-07-03T20:22:42.357
6@JuliePelletier The ratio of false positives is heavily influenced by the actions of the user. I never have a virus, malware or anything like that because I'm very carefull. This automatically makes that most (if not all) detections are false positives. I do still use an anti-virus of course :). – Mixxiphoid – 2016-07-04T08:25:36.377
@Mixxiphoid: I have an AV installed for the rare times I do risky downloads but most of the time it's off. – Julie Pelletier – 2016-07-04T15:01:55.767
3@Mokubai It is an interesting idea that a virus could cause havoc by adding viri signature to legitimate files - making the av do the dirty work. – emory – 2016-07-04T22:31:21.090
1@emory ... Wow. Somebody needs to write a (buggy, easy to defeat, non-spreading!) proof-of-concept implementation and send it to antivirus companies. – wizzwizz4 – 2016-07-10T10:08:01.793
72
For the same reason that (most) governments arrest suspected criminals instead of shooting them on the street at the slightest provocation:
You want to give the suspect a chance to defend themselves, in case they actually did not commit any crime at all. And, even if they did commit a crime, you probably want to find out all about it.
38By that analogy, there should be at least some antivirus that delete by default... – PlasmaHH – 2016-07-03T15:31:50.370
@LightnessRacesinOrbit KAV15 does not "exist" anymore; KAV16 was released in 2015 in order to be conpatible with Windows 10. – EKons – 2016-07-05T10:24:25.930
5
@ΈρικΚωνσταντόπουλος: What a ludicrous statement. Does Windows 7 also "not exist"?
– Lightness Races with Monica – 2016-07-05T10:40:35.6101@LightnessRacesinOrbit KAV15 does not " exist " anymore; KAV16 was released in 2015 in order to be conpatible with Windows 10. I put "exist" in quotes. It is not compatible with Windows 10, and will die when 8.1 dies. – EKons – 2016-07-05T10:44:14.897
9@ΈρικΚωνσταντόπουλος: People will be using Windows 7 and 8 for a long time. There is nothing "nonexistent" about a one-year old piece of software. Don't be so silly! – Lightness Races with Monica – 2016-07-05T10:52:38.713
3@LightnessRacesinOrbit Actually, using any OS after its end-of-life for production is dangerous and must be avoided to the greatest possible extent. – EKons – 2016-07-05T10:55:46.070
14@ΈρικΚωνσταντόπουλος Windows 7 has extended support until 2020, mate; Windows 8 until 2023. I'm struggling to detect your point. What is it? – Lightness Races with Monica – 2016-07-05T10:57:06.613
@LightnessRacesinOrbit It's like using Windows XP after Apr 8, 2014. It's just dangerous, especially when the OS is Windows, since viruses will be targeted there. When Windows 8.1 SP1 extended support ends, viruses will start targeting that. – EKons – 2016-07-05T11:02:00.380
20@ΈρικΚωνσταντόπουλος Yes, in 2023. What is your point? – Lightness Races with Monica – 2016-07-05T11:08:19.440
2(replacing bizarrely-silently-deleted comment, thanks a lot, Moderators) @PlasmaHH Kaspersky Anti-Virus 2015 = USA – Lightness Races with Monica – 2016-07-07T16:20:08.003
1
Viruses (for example) are not necessarily a "stand-alone" binary (.exe). Traditionally, many of them "attach" themselves to (many) normal executables. (hence the choice of the word: "infect")
Therefore "deletion" of the malware file is not the only option. Many AVs offer the option to "clean" the infected files. (remove the virus part from otherwise normal program files. leave normal program where it is.)
"Spreading of the infection" would then not be based on "running the malware" (visible process .exe) -- but based on running any "normal program" (Word, Excel). (or open a normal document with those)
Moving the "normal but infected" program file to a quarantine location, is a first step to stop spreading the infection. There, it is less likely to be continuously executed during every day operation.
Quarantine gives you options, before deletion. In case the "cleaning" failed. In case you have a "better tool" somewhere else. Or in case you still need all those infected files. (for analysis, data recovery)
0
Just sometimes anti viruses might consider your important files as malicious and instead of automatically deleting them it quarantines them where they can't execute or access your files and notifies you of its actions.
Welcome to Super User! This answer adds nothing new to the thread. Please read the other answers before posting something as an answer. – rahuldottech – 2016-07-31T07:50:19.470
123A few weeks ago ClamWin AV started detecting all
docxfiles created in Polish version of Word as malicious. I don't use ClamWin myself, but I guess those who do were grateful for having quarantine. – gronostaj – 2016-07-03T19:47:34.01010
This discussion spawned a related Sec.SE question.
– Ben N – 2016-07-04T19:30:01.723What about false positives? – EKons – 2016-07-05T10:19:46.307
5Almost every single anti-virus program I've used lets you choose what happens when a particular threat is detected (whether it ignores, quarantines, or deletes the suspected file...). – Breakthrough – 2016-07-05T19:04:35.233
8To the ones asking to close this question as opinion based: there are reasons to put files in quarantine that are not opinion based: false positive, future possibility to recover the file,partial recovery of the infected file, possibility to study the virus... The choice to keep or not to keep them can be eventually personal, even if not completely arbitrary: indeed if a file is a distributed one (a program part) it is possible to copy/download it from a safe source and replace the original with no need to keep the infected copy. No chance instead for the ones made by us(here personal) – Hastur – 2016-07-06T10:14:23.523
6Many years ago an AV package whose name I won't mention (coughSymanteccough) decided to flag hundreds of system DLLs as infected during a routine overnight scan. Naturally, quarantining half the operating system didn't go over well when Windows was rebooted. The machine was completely bricked and couldn't be booted even in safe mode. So I had to remove the HD from the machine, put it in another machine as a second drive, and move the DLLs back where they belonged. This took a full day to accomplish. Consider what would have happened if those files had been deleted instead of quarantined. – Carey Gregory – 2016-07-06T18:47:20.167
@Breakthrough INterstingly enough, most AVs I've used actually split up detection and deletion entirely.. The settings I've useen let you choose between "Ignore" and "quarantine" upon detection, with a separate setting entirely for "delete items in the Quarantine after __ days". Never seen an option to immediately delete a potentially unwanted / malicious file. – WorseDoughnut – 2016-07-07T15:55:20.640
@WorseDoughnut Microsoft Security Essentials has just Quarantine and Remove. – Breakthrough – 2016-07-08T00:35:14.503