6
1
In the past I have always run a NAT router between my Windows PC's and the internet. I'm wondering if I still need this or whether the OSX firewall is good enough to let me put a Mac directly on the internet.
6
1
In the past I have always run a NAT router between my Windows PC's and the internet. I'm wondering if I still need this or whether the OSX firewall is good enough to let me put a Mac directly on the internet.
7
Though I don't mind hooking up my Mac to any network, I don't have the definitive answer. Still, some notes too long for a comment:
The OS X built-in firewall is an application firewall: accepting incoming connections is granted per application, not per port. Once granted permission, an application could open any port it likes, but I guess that's not an issue for software you trust. Also, it only applies to incoming connections: all outgoing connections are always allowed (but that is true for a NAT-firewall as well). And according to Apple's "Mac OS X 10.5 Leopard: About the Application Firewall":
All applications [..] that have been digitally signed by a Certificate Authority trusted by the system [..] are allowed to receive incoming connections. Every Apple application in Leopard has been signed by Apple and is allowed to receive incoming connections.
In 10.6 the latter is made more explicit (and can be disabled) as "Automatically allow signed software to receive incoming connections. Allows software signed by a valid certificate authority to provide services accessed from the network.":
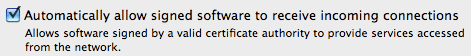
Hence, even when the firewall is active, every server-like Apple application that you have running is, by default, allowed to accept incoming connections. (Or, maybe in 10.6 it even applies to any signed application?) A bug in such software could compromise your computer. I don't know how that affects things like Bonjour and file sharing.
If the firewall is active then any non-Apple software (or at least unsigned software) first needs your permission to accept incoming connections. When such software is updated, it might or might not need your permission again:
A signed application [..] can mathematically prove that it is indeed a new version of the same application from the same vendor that you expressed trust for in the past. The result is an end to dialog boxes asking you to confirm a choice whose safety you have no reasonable way to verify.
5
Of course one could go on about how in theory nothing is safe, ever, and all that.
But for practical purposes, yes, it's generally safe enough to put your Mac directly on the internet. (Everyone does it – well, most people in any case – and it's very unlikely anything bad will happen to you.) Especially if you do not open any extra services (like httpd, etc) on your machine.
That said, do (let the automatic updater) keep your Mac OS X always up-to-date with latest security fixes, and check that its built-in firewall is enabled.
2Probably a good idea to make sure the firewall is turned on (it's disabled by default in some versions of OS X). – Paul R – 2010-02-16T11:15:27.407
Everyone does it -- that's definitely not true. – Arjan – 2010-02-16T11:28:02.493
Well, most people, whatever. For practical purposes "everyone". ;) – Jonik – 2010-02-16T12:38:13.557
You also probably want to make sure your firewall, the one built into OSX, is set to stealth mode. – Darren Newton – 2010-02-16T12:41:29.610
Well, I certainly wouldn't. But then, I'm not a Mac user either. – Quandary – 2011-06-24T18:48:34.793
2
It's never secure to connect a computer to the internet, and it's always better to have a router in between.
Since most routers run embedded-Linux, it's most-likely more secure to have them in-between.
Speaking as a Linux-user: Mac OSX has most of the applications from FreeBSD, so make absolutely sure you have ssh and sshfs not installed or running, if you don't need them.
And just having a firewall is not enough. Make sure it's properly configured.
May I ask: Why the downvote ? – Quandary – 2010-02-21T11:44:59.643
Wondered the same thing ..... ? – JRobert – 2010-06-16T22:44:04.683
1
Who would ever make a router from WinCE? That is crazy talk. OMG. http://www.marvell.com/company/news/pressDetail.do?releaseID=283 people did it.
– nycynik – 2018-01-12T13:47:52.680I didn't downvote, but I would say that it isn't safer because it runs Linux (which is only as secure as how well configured it is anyway) but because it's a router and that is its function. – Ben Richards – 2011-09-19T06:29:14.283
@sidran32: I disagree. A router needs an operating system, and it's only going to be as secure as the operating system, the weakest link. And if that OS was WindowsCE, then I'd rather not put a router in between. In that sense, the "always better" was probably the reason. – Quandary – 2012-10-30T06:00:33.067
1
Considering you're not be running something like IE6 out of the box (unlike a fresh XP install for example) you should be fine.
As always, it's what you DO on the internet which ultimately effects the security of your system. If you're downloading lots of files from lots of sources and clicking every link that comes your way then you're at a higher risk (of course, if you take the right security precautions you'll be right)
As the others have said, nothing on the internet is technically 100% safe. Mac's are less vulnerable... but by no means invulnerable.
Note that Safari is not any better than IE6 when it comes to security. Well actually, Safari is worse... – Quandary – 2011-06-24T18:49:59.083
1
I have a NAT ADSL connection at home and a 3G service for away. While on 3G I have noticed ssh login attempts which you would not normally see behind a NAT firewall.
Have a look to see what services you are running.
netstat
or
netstat -f inet
Active Internet connections
Proto Recv-Q Send-Q Local Address Foreign Address (state)
udp4 0 0 *.ipp *.*
udp4 0 0 172.16.250.1.kerberos *.*
udp4 0 0 192.168.144.1.kerberos *.*
udp4 0 0 *.* *.*
udp4 0 0 localhost.ntp *.*
udp4 0 0 *.ntp *.*
udp4 0 0 *.snmp *.*
udp4 0 0 *.* *.*
udp4 0 0 *.mdns *.*
udp4 0 0 *.* *.*
udp4 0 0 *.syslog *.*
icm4 0 0 *.* *.*
This is an abbreviated list of what I am running. You can see snmp and a syslog server which you probably would not have.
Most services are listening on all interfaces (*.). In my case I should fixup my snmp and syslog to only listed on my local network.
Install nmap http://nmap.org/dist/nmap-5.21.dmg. nmap has lots of different ways to see if a service or port is listening - try out some on your machine, but not on other machines unless you know what you are doing (I certainly don't).
nmap 127.0.0.1
Starting Nmap 4.85BETA6 ( http://nmap.org ) at 2010-06-17 00:09 EST
Interesting ports on localhost (127.0.0.1):
Not shown: 960 closed ports, 32 filtered ports
PORT STATE SERVICE
22/tcp open ssh
88/tcp open kerberos-sec
139/tcp open netbios-ssn
445/tcp open microsoft-ds
548/tcp open afp
625/tcp open apple-xsrvr-admin
631/tcp open ipp
5900/tcp open vnc
Nmap done: 1 IP address (1 host up) scanned in 6.28 seconds
Try nmap from another machine as well - you will have to install it there as well. Windows and Linux versions are available.
Are there services you don't want running?
In my case, i'm not sure why I am sharing files via samba (139/445) so I'll turn that off.
I can't see how to turn off ipp (631). This is for printer sharing which is turned off.
If I go online and nmap my pppd IP address, the ipp port is closed. This is good and matched the cupsd config file.
I don't need AFP running all the time so I'll turn that off.
I don't need ssh or screen sharing running so I'll turn that off as well.
I now just have these running.
88/tcp open kerberos-sec
625/tcp open apple-xsrvr-admin
631/tcp open ipp
Someone mentioned that most people are behind a NAT firewall. This is probably true if you have a router, but check that NAT is turned on.
But on a 3G service you are directly connected so you should be careful. I haven't been, so this was a good question to make me review my settings.
Other things to do.
appfirewall.log fileipfw rules.Remember, if a service is not running, no one can get in. So the fewer ports that are opened the better.
0
It is not safe to put anything on the internet. Having said that, nowadays most people connect to the internet behind a router, which also tend to implement firwalls and whatever else, so you could be using win95 without a hitch.
It all depends on what you do with that computer and if you are only browsing the internet or are serving content. Can't answer anything more specific without further details.
+1 Informative, in-depth answer (compared to my answer, anyway :) – Jonik – 2010-02-16T14:44:56.757