First, access token
contains much more than the security identifier (SID). One only has to "Run as administrator"
a program to see in the Task Manager that its user is oneself and not
Administrator, and this miracle is achieved just by the modification of the
access token, not by replacing the SID.
Second, NT-AUTHORITY and SYSTEM are neither accounts nor groups,
in spite of what say various other sources (even inside Microsoft).
An SID usually has a name that is displayed whenever required.
A user account will contribute its SID as principal SID to the access token,
which will also determine the name displayed by various utilities.
But the access token may contain additional SIDs, for example for all the groups
to which belongs that user account. When checking permissions, Windows will
look for any SID in the access token that has that permission.
Some well-known Windows SIDs will have names reported by Windows,
although they do not really belong to any account.
A Security Identifier
is defined by Wikipedia as :
a unique, immutable identifier of a user, user group, or
other security principal.
The SID does not need to even define a user account or a group.
It just defines a set of permissions. The above Wikipedia article adds:
Windows grants or denies access and privileges to resources based on
access control lists (ACLs), which use SIDs to uniquely identify users
and their group memberships. When a user logs into a computer, an
access token is generated that contains user and group SIDs and user
privilege level. When a user requests access to a resource, the access
token is checked against the ACL to permit or deny particular action
on a particular object.
The SID of NT-AUTHORITY\SYSTEM can be added to other accounts.
For example, this is said about the
LocalSystem Account:
The LocalSystem account is a predefined local account used by the
service control manager. [...] Its token includes
the NT AUTHORITY\SYSTEM and BUILTIN\Administrators SIDs;
these accounts have access to most system objects.
One can already see in the above text the confusion that reigns even in
Microsoft documentation as regarding system SIDs, which are not exactly accounts nor groups - which are just a set of permissions.
This confusion further extends to other utilities and articles, so any
returned information should be carefully examined.
The Microsoft article
Well-known security identifiers in Windows operating systems
details all system SIDs, some of whom I include below:
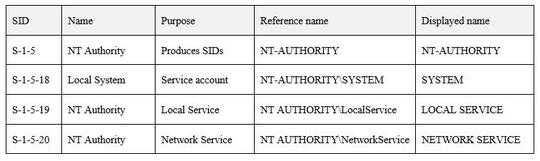
Conclusion: NT-AUTHORITY\SYSTEM is the name of a Security ID,
which is neither a group nor an account.
It is displayed in Task Manager as SYSTEM when it is the principal SID of a
program. The most I would call it is "a pseudo account".
 .
(Using the internal Win32 API LookupAccountSid also reveals that it seems to be a group SidTypeGroup.)
.
(Using the internal Win32 API LookupAccountSid also reveals that it seems to be a group SidTypeGroup.)
This maybe answer your? question here: http://superuser.com/questions/471769/what-is-the-nt-authority-system-user/471774
– XsiSec – 2016-04-19T12:32:53.137You are right my bad apologize – XsiSec – 2016-04-19T12:38:16.150
SIDs don't have to be either of those, do they? – user1686 – 2016-04-25T05:59:13.583