That's because your antivirus software is attacking you via a man-in-the-middle attack. Or at least that's the possibility I'll talk about below.
People have downvoted this answer and demanded evidence for my claims. Fortunately, someone already added links in the comments. Kaspersky, Bitdefender (see next mention of the word "Bitdefender"), and avast! do this for sure. I don't know about the others. You can also watch this video about it. (Unfortunately, the video is in German but you'll still be able to see what's happening even if you don't speak German. Start watching at 1:40 in this case.)
Go onto a https page (like the GMail website) and click on the small lock left of the address bar of your browser.
Then you have to figure out how to get information about the connection. In Firefox, you have to click onto the arrow button on the right. You already see what you need to see but click onto "More Information" anyways. A window like this will be shown:
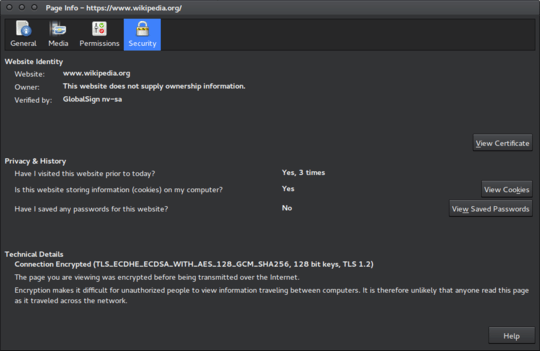
As you can see, I visited Wikipedia to create this screenshot and the identity of the website is verified by GlobalSign nv-sa. In your case, you will see the name of your antivirus software or something related to that.
What's happening here is that the antivirus software is directing your browser's traffic through a software it provides. To it intercepts your browser's traffic through man in the middle.
I'm calling this a man-in-the-middle attack not only because it follows the same principle as a malicious man-in-the-middle attack but also because it can severely increase the vulnerability of your system if malicious software (the authors of which can't sign certificates themselves and therefore not intercept your https traffic without you noticing) uses your antivirus software to read the traffic. Furthermore, Bitdefender severely decreases the security of the connection as you can see in this video at 4:38 or by trying it yourself. The user – of course – isn't told this and therefore is attacked by the software they use to defend themselves. Even if it didn't harm the user, it'd still be a man-in-the-middle attack according to definitions you can find online (including the one on Wikipedia).
This is easy enough to do with http. But if you're using https, you'd think that the antivirus software can't read anything. But it can because you're not connecting securely to the webserver but to your antivirus software. It then reads the traffic, manipulates it if it wishes to do so, and encrypts it again. (So there is a secure connection between your antivirus software and GMail.)
Your antivirus software can then just do with your emails (Or any other traffic!) whatever it wants.


Seemed to be security-related, where else could I ask it? – hirse – 2016-04-17T09:47:19.753
1@hirse: My guess is that you have a Firefox extension from Avast installed. Such extensions have access to the plain text data, i.e. before encryption. – Steffen Ullrich – 2016-04-17T09:58:52.167
@SteffenUllrich, I cannot find an extension or plugin from avast in the Firefox Add-on Manager. – hirse – 2016-04-17T10:13:58.287
2If its not done with a Firefox extension than they do SSL interception, i.e. you would see their MITM CA as trusted in the browsers CA store. Although the browser is then probably configured to use a (local) proxy. – Steffen Ullrich – 2016-04-17T11:48:27.350
It seems that Avast is using different methods for different browsers as this answer explains. Firefox shows legitimate certificates, so I guess they use number 1 for it. With Edge they seem to be proxying with their own root CA.
– techraf – 2016-04-18T05:40:45.620