0
I'm trying to email myself a utility (HJSplit) because I can't download it directly on my work computer. Of course, my company's filters are there to stop me from doing exactly this. But darn it I'm trying get some work done, and I can't open this 500 MB log file without splitting it first. (Notepad can't even handle 100 MB. And UltraEdit crashes for some reason, even though it should be able to handle it.)
I opened the ZIP of the utility in a hex editor (UltraEdit) and modified a few bits, and changed the extension to JPG. This made it past Gmail's no-executables rule, but still got blocked by my company's Exchange server.
Regardless the (a)morality of what I'm doing, I'm curious, what bits need to be changed to make the nature of a file indistinguishable or unidentifiable (or identifiable as a benign type) to a filter?
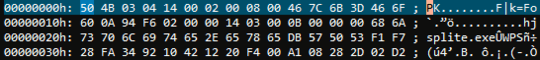
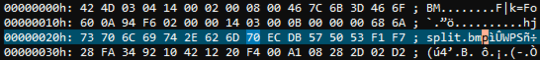
inb4 Moral Orel tells us to respect company policies and that I should talk to my IT staff. That's fine and I may very well end up doing that since this has taken longer than simply asking, but I'm still curious as to whether it's possible to change "magic bytes" to fool filters. – Andrew Cheong – 2016-01-08T22:46:34.280
Exchange server might be sniffing the file, zip it up and password protect it, see if goes through. – Moab – 2016-01-08T23:25:06.983