1
I am creating three level of certificates,viz, Root->A->B . A is signed by root and B is signed by A . The certificates are generated using OpenSSL command line utility for windows.
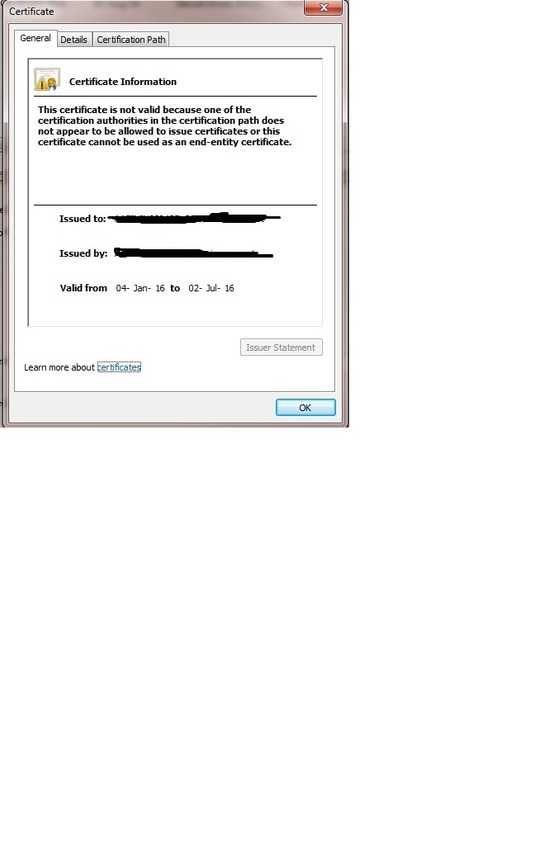
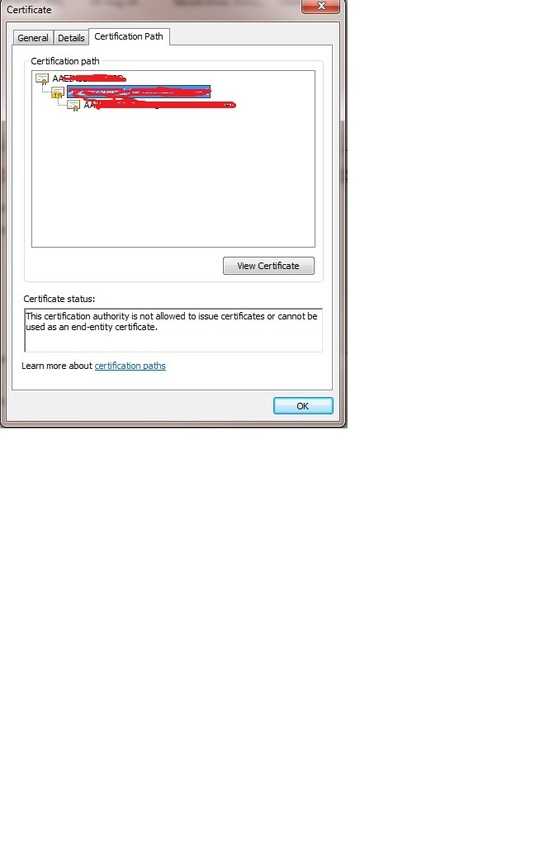
The certificates are created successfully and i installed them in Win7.Now the problem is with the Certificate 'B' . Attaching the screenshots
I am following the steps provided in the below blog on how to create a root and subordinate and get the subordinate signed by the root-
blog.didierstevens.com/2015/03/30/howto-make-your-own-cert-with-openssl-on-windows/.
Can someone help me with what i am doing wrong? Basically i am trying to create certificate chain and navigate to the root certificate given any intermediate.
1Welcome on Secrity SE. While this question talks about using certificate, it deals merely with an end-user's issue and seem therefore most suited on [su] which is dedicated to computer's enthusiasts and power users. Be sure to mention in your question if you have also correctly imported the other certificates composing the chain in your Windows certificate store and if the root correctly appear the other trusted roots. – WhiteWinterWolf – 2016-01-04T11:37:29.683
3It appears your certifiate A is not allowed to be used as an intermediate. Check the purpose of the certificate and make sure the certificate is allowed to be an intermediate CA. – BadSkillz – 2016-01-04T13:07:12.370
To search before posting a question, and to ensure future visitors can find it when searching, next time please add the error messages as text, not (only) as an image. Also, please crop the images. Thanks. – Arjan – 2016-01-04T18:19:43.030
@WhiteWinterWolf ,Thank you for the welcome. Will keep such points in mind before posting next time. BadSkillz,Will check that and revert Arjan, Will keep in mind. Thanks – user1242010 – 2016-01-05T06:09:02.897