342
131
I need to download an SSL certificate of a remote server (not HTTPS, but the SSL handshake should be the same as Google Chrome / IE / wget and curl all give certificate check fail errors) and add the certificate as trusted in my laptops Windows' certificate store since I am not able to get my IT guys to give me the CA cert.
this is for office communications so I cannot really use the actual client to get the cert.
How do I do this, I have Windows 7 and a pile of Linuxes handy so any tool / scripting language is fine.
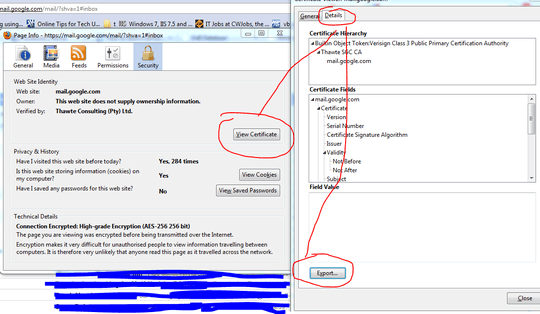

To get the certificate of a mail server, see http://security.stackexchange.com/questions/70528/how-to-get-ssl-certificate-of-a-mail-server
– That Brazilian Guy – 2017-02-16T15:56:41.463Most likely, your browser has a built-in feature for this -- maybe under "developer tools". – nobar – 2019-08-22T20:07:10.307