Are you open to running Windows 8? Do you have a TPM chip in your laptop, and is your laptop UEFI capable?
There are TCG OPAL SSD drives out there. I have not found a Sandforce based drive that supports this, but Micron has one: Micron C400 SED. You have to make sure you buy the SED version, not the plain version. Using an OPAL compliant drive will allow you to use Bitlocker in Windows 8 in conjunction with the drive's encryption (which it's already doing).
Bitlocker in this scheme does not actually do any encryption from the system side (at least for data read/written). The bulk of Bitlocker in this mode is acting as a "Gatekeeper" since SED drives still need a means of access control to unlock the drive. When those are activated in this mode (with W8 and Bitlocker), the drive is initially locked and the system will only show a very small "shadow partition" under 200MB. This is where the W8 boot files are stored and the unlocking in Bitlocker happens with it interacting with TPM to pass a key to unlock the drive.
If you don't want to go Windows 8, you lack TPM (though I assume you have it since they asked you to enable bitlocker), or BIOS instead of UEFI there are a number of software products that can manage SED drives in place of Bitlocker.
In my experience, Bitlocker does in fact have a noticeable degradation in performance even with HDDs. With SSDs, the comparisons I've seen seem to indicate the degradation is worse, perhaps enough that a lot of the benefits to SSD is reduced. In my view, a SED based SSD with Bitlocker management (or another software piece) is the best way to go.
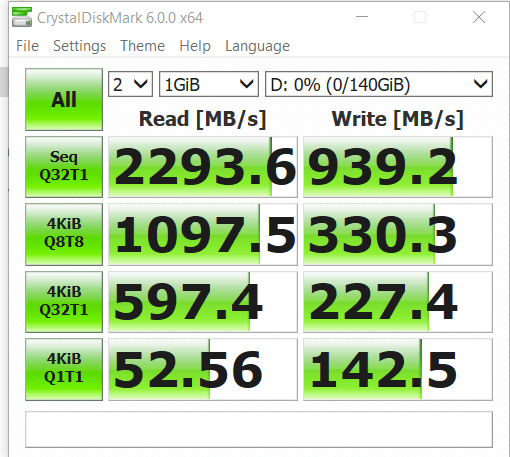
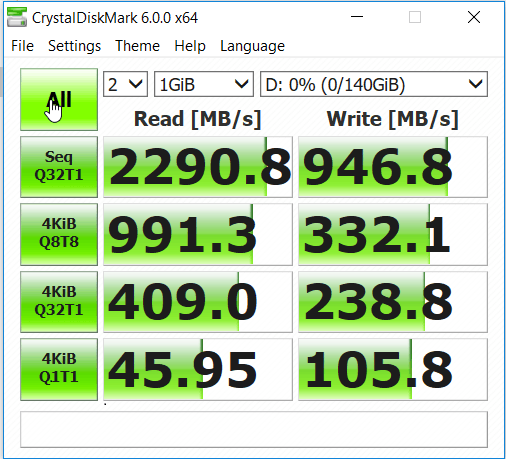
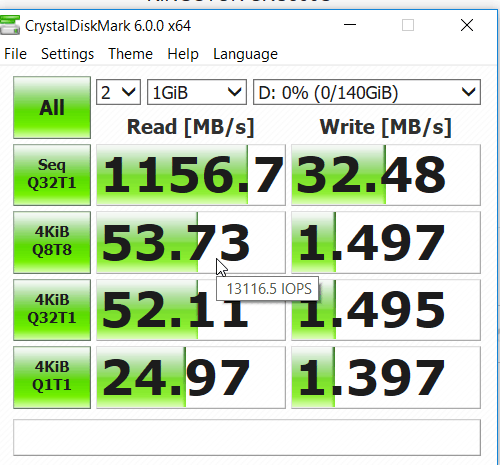
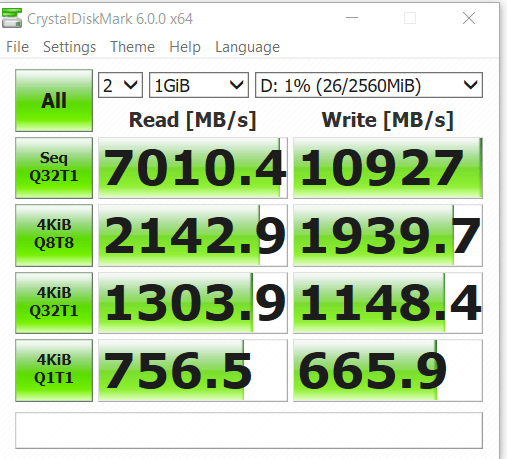
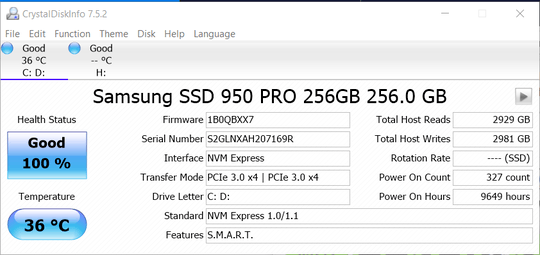
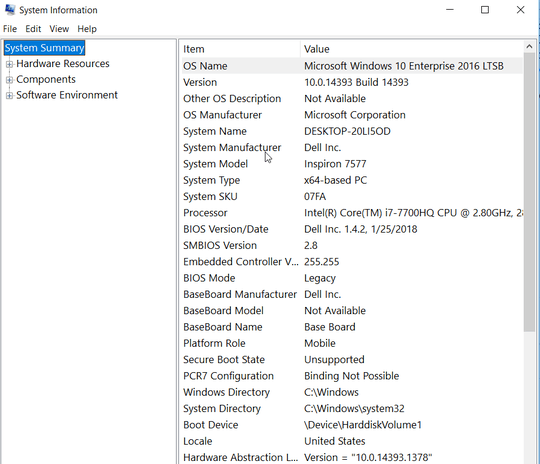
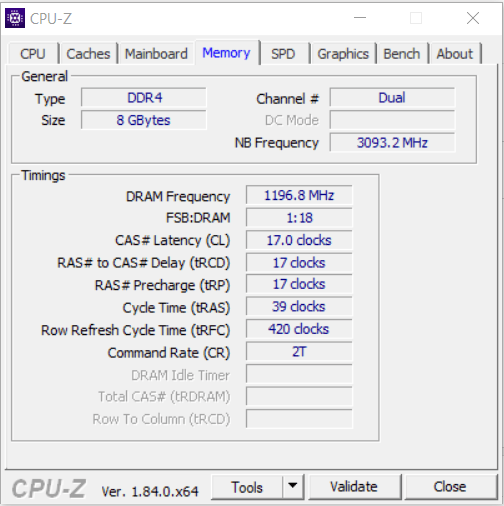
See post #8...http://forum.notebookreview.com/lenovo-ibm/473894-enable-bitlocker-not-whats-benefit-trade-off.html
– Moab – 2011-01-19T22:21:30.800Bitlocker FAQ...http://technet.microsoft.com/en-us/library/ee449438(WS.10).aspx
– Moab – 2011-01-19T22:23:15.323Microsoft Blog, nice reading...http://blogs.msdn.com/b/e7/archive/2009/05/05/support-and-q-a-for-solid-state-drives-and.aspx
– Moab – 2011-01-19T22:25:09.763related: http://superuser.com/questions/204635/how-much-will-full-disk-encryption-slow-down-a-netbook/204642#204642
– akira – 2011-01-19T23:39:55.643