14
2
I am managing a small business network with a number of Windows 10 and 7 PCs. Intermittently but quite frequently users complain that they can no longer access shared folders with other co-workers. Quick troubleshooting determines that the issue is due to the infamous "Unidentified Network detected" which then applies the "Public" network profile instead of "Private" network profile, thus Homegroup/file sharing, etc. does not work. From my searching this is a common problem for many users. I do not see any proposed solutions that work.
Environment:
- All Windows PC are connected via wired Ethernet (though they may have a Wifi NIC)
- They are all connected to a 48 port Avaya L2 managed switch, all on the same 10.10.10.x subnet
- The switch is connected to an Asus RTN-66U home router
- The Asus router connects to Cable modem
- The Asus router provides DHCP to Windows machines
- I have configured the router with DHCP reservations for each Windows PC, i.e. PCs always get the same IP address on bootup
- No domain controller
Problem:
Even though I have configured all Windows machines active network profiles = Private, they frequently (every couple of weeks or so) revert back to Public, which prevents file sharing etc.
Fixes attempted:
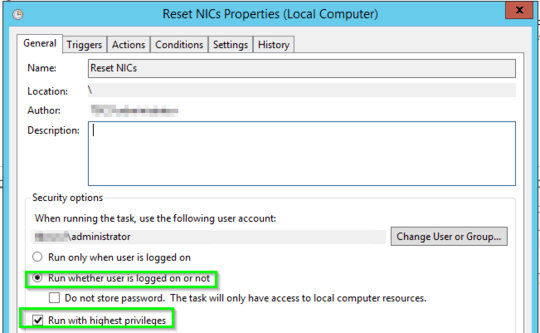
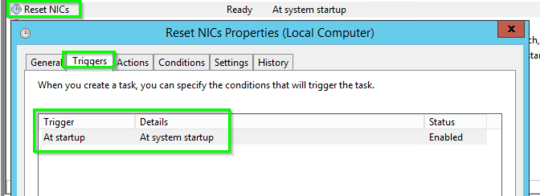
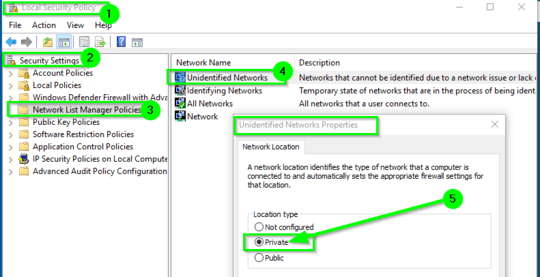
On each Windows PC I have modified the Local Group Policy Computer Configuration->Security Settings->Network List Manager Policies:
- Unidentified Networks = Private
- Identifiying Networks = Private
Observations:
I believe the issue is that the Windows Network Location Awareness (NLA) service is detecting a new network which causes a new Network Profile to be created which then defaults to Public (even though above I have configured the Local Group Policy to default to Private).
Many of the computers show that Windows has detected a new Unidentified Networks many times, i.e. they show "Network 14", i.e. there are 14 different network profiles. I see these multiple profiles when reviewing the profiles here in the Registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles.
All 14 profiles are when the computer was actually connected to the same network described above.
I have not been able find a resource that describes exactly how NLA generates a unique identifier for a network and thus why it might detect that it has discovered a new network.
Question:
How do I keep Windows from incorrectly identifying my local network as a new network? Perhaps it would help if I knew what steps NLA follows to generate a unique identifier for a network?
1
I edited your question a bit to help focus it on asking about solving the actual problem. See XY problem.
– I say Reinstate Monica – 2018-01-08T22:59:30.740NLA identifies a network based on the MAC address of the default gateway specified for that network adapter. Is it possible your router has become inaccessible to these computers? Does the problem seem to affect multiple computers in a short window of time, or is it only one user one day, then another user at a completely different time? – I say Reinstate Monica – 2018-01-08T23:09:09.793
Perhaps look at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged or at least around that location in the registry - and see if the DefaultGatewayMAC and DNSSuffix match what you expect – Ross – 2018-01-08T23:44:34.657
PaulH - Check out my answer when you get a moment, this is what I've used with rather solid success in a production environment as I put in the Method 1 section but I also provided more detail with the Method 2 section of my answer. I hope you find any of these solutions as helpful as I have for this issue. – Pimp Juice IT – 2018-01-12T17:23:23.873