Mp3blaster is a terminal mp3 player running a UNIX-like operating system, e.g. Linux, Free/Net/OpenBSD, etc. I usually use this player for playing my music, but yesterday I found a blog which claim that there is an exploitable 0day.
1) The vulnerability is found in file main.cc. This is the code:
void
warning(const char *txt, ... )
{
va_list ap;
char buf[1025];
mw_clear();
move(LINES2,1);
attrset(COLOR_PAIR(CP_ERROR)|A_BOLD);
va_start(ap, txt);
vsnprintf(buf, 1024, txt, ap);
va_end(ap);
addnstr(buf, (COLS > 14 ? COLS 14 : 1));
attrset(COLOR_PAIR(CP_DEFAULT)|A_NORMAL);
refresh();
}
The vsnprintf () function uses the parameter as txt format string. warning () is called from fw_convmp3 (), a function that is invoked when the user wants to convert a WAV file to MP3 format:
void
fw_convmp3(const char *tmp, void *args)
{
char **selitems;
...
...
if (!(decoder = new Mpegfileplayer(Fileplayer::AUDIODRV_OSS)) ||
!decoder>openfile(file,
file2write, WAV) || !decoder>initialize(NULL))
{
sprintf(bla, "Decoding of %s failed.", selitems[i]);
warning(bla);
selItems [i] contains the name of the file that the user wishes to convert. The bug can be reproduced as follows: a file named "% n.mp3" blank is created, and F1 is pressed within mp3blaster to select it, then press F6 to invoke the function of conversion, the program will apply for a WAV directory to save the converted file, press ENTER et voilà!
2) Examples
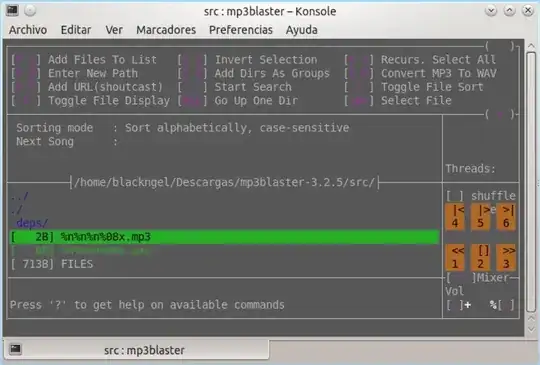 Figure 1: The file that exploits the bug was selected
Figure 1: The file that exploits the bug was selected
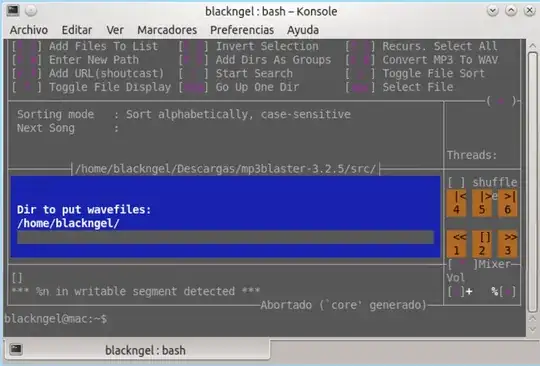 Figure 2: When it comes to saving with F6 bug occurs
Figure 2: When it comes to saving with F6 bug occurs
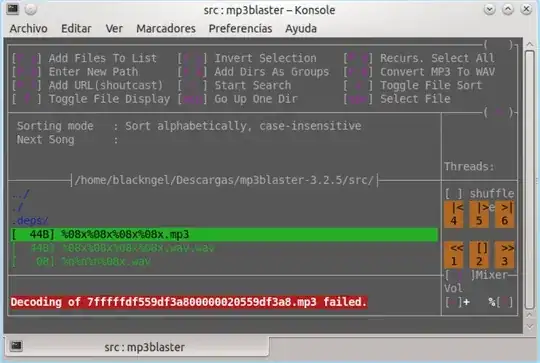 Figure 3: Exploiting the bug
Figure 3: Exploiting the bug
So my question is:
How this vulnerability can affect my operating system?
For example:
If I download free mp3 from any legal site and some song comes modified like the above example is it possible to load keylogger or trojan in my OS?
Information Source: elladodelmal blog