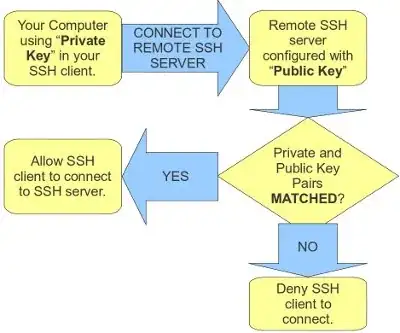
I think this question can be considered from two different angles: security and convenience.
When we create a SSH key pair, we are asked for providing a passphrase to add a more layer to protect the private-key, as following:
$ ssh-keygen -t rsa -b 4096 -C 'With_OR_Without_Passwd'
Generating public/private rsa key pair.
Enter file in which to save the key (/Your/HomeDir/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Although there is an explicit prompt asking for passphrase, but some (or many) people still focus more on the information in brackets: (empty for no passphrase), and following that suggestion.
Combining whether or not using multiple SSH key pairs and whether or not enter additional passwd, we have at least four ways to go. And let's assume all key-pairs and the config file are stored in ~/.ssh/.
Now let't consider security first.
The following table gives a simple rank about security (larger number means more secure):
Security Ways to go
1 One SSH key-pair (NO passwd)
1 Multi SSH key-pairs (NO passwd)
2 One SSH key-pair (WITH passwd)
2 Multi SSH key-pairs (WITH passwd) (SAME passwd)
3 Multi SSH key-pairs (WITH passwd) (DIFF passwds)
Without passwd, if our system is intruded by someone, then the breaker can get all of our private-keys and config, also the authentication of remote servers. So in this situation, One key-pair and Multi key-pairs are the same. The most secure way is to use different passwds for different ssh key-pairs.
Then let't think about convenience.
But more key-pairs and more passwds also make our life less convenient, the following table gives a simple rank about security (larger number means more secure):
Convenient Security Ways to go
5 1 One SSH key-pair (NO passwd)
4 2 One SSH key-pair (WITH passwd)
3 1 Multi SSH key-pairs (NO passwd)
2 2 Multi SSH key-pairs (WITH passwd) (SAME passwd)
1 3 Multi SSH key-pairs (WITH passwd) (DIFF passwds)
So, in general situation, if we have to trade off with security and convenience at the same time, we can multiply the two scores, and maybe One SSH key-pair (WITH passwd) is the good one to choose.