0
From Chapter 18 of Significant Digits, a fan-fiction of the Harry Potter and the Methods of Rationality fan-fiction, we have the following cryptographic problem:
As it happened, the books were unnecessary. By the time Pip appeared at the door with four books in hand, fifteen minutes later, the puzzle was solved.
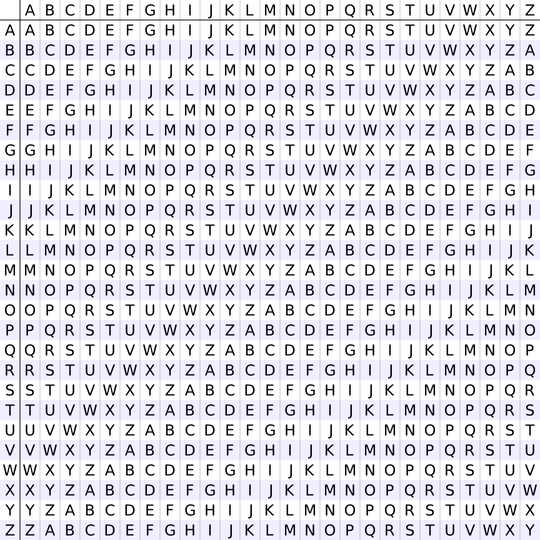
Harry was able to draw the square from memory: the tabula recta, one of the most basic and famous ways to use a running-key cipher. It was almost five hundred years old, and fairly famous among cryptographers: a table that was 26 letters tall and 26 letters long, with each row and column beginning one letter further in the alphabet (the first row started A, B, C … , the second column was B, C, D …, etc). It was a simple and elementary way to use a specific key to encode your text.
There was no 33rd part to the Treaty for Health and Life, and so Harry guessed that the third part of the third section -- that is, 3.3 -- was the indicated key. It took less than a minute to verify with the first six letters of the cryptograph, moving letter by letter through the key. He looked in the tabula recta for the A row, then located the cyphertext letter T in that row. That T was in column T, and so the first decoded letter was T. Next he found the coded U in row N, resulting in an H.
tuccnimechlxbguhvpesyvbsuxihryccmcptwkxcfmbpemvjvhahxdwvqmbrfwfkkiiwbivplvogiyeelwalvjmvaewdiibeexbvrtotewrkecbxrfuukepjgjsfjkaxdmcztbafmnqfstfkbtnxkmssurna
Anyattemptstosabotagedisruptdelayrepurposealterorotherwiseinterferewiththeoperationsoftheaforementionedtransportregardlessofwhetherornotsaidsabotagedisruptiondelayr
It only took three letters to know he was correct, as the message began:
T H E
Your job is to code-golf a program that deciphers text, using the algorithm illustrated above.
It should:
- Accept the ciphertext string as input.
- Accept the key text as input.
- Output the decoded plain-text.
You may assume that the ciphertext and key text are the same length. Your program is permitted to explode if the ciphertext and key text have different lengths.
You may assume all input consists of lowercase letters a-z. Your program is permitted to explode if any other characters are entered.
This is code golf. Shortest program wins.
I wasn't aware of the local customs. Question edited. – Li-aung Yip – 2015-08-22T17:58:02.343
No worries, some languages have a hard time with certain requirements is all. It would also be a good idea to provide the whole resulting string from your example. – FryAmTheEggman – 2015-08-22T18:00:04.160
3PS On the basis of the excerpt quoted, the author of that fanfic seems to have confused Harry and Hermione. – Peter Taylor – 2015-08-22T18:05:01.433
1
@PeterTaylor: Not an exact duplicate - this question, as asked, has stricter restrictions on the input and should permit a shorter answer. Also, in this particular fanfic, Harry really does know these things; see http://hpmor.net/ for an entertaining and educational re-imagining of Harry Potter.
– Li-aung Yip – 2015-08-22T18:07:23.7002It's not exact, but it's pretty close. Using a smaller alphabet doesn't change much at all, and making a one-time pad instead of a repeating Vigenère key just saves a string repeat or a mod operation. – Peter Taylor – 2015-08-22T18:13:33.747