7
2
Your task is to devise a programme that extracts the bits, in order, represented by the first argument based on the set bits represented by the second argument (the mask).
Formal Definition:
Let the first argument
xrepresent the binary stringS=(xn)(xn-1)...(x1)withn>=0andx1being the least significant digit andxn = 1.Let the second argument
yrepresent the binary stringT=(ym)(ym-1)...(y1)withm>=0andy1being the least significant digit andym = 1.Let the result represent
0ifxrepresents 0 oryrepresents 0.Let the number of
1digits inTbep. Let{di}, i in [1, p]be the set of binary strings of the form(dim)(di(m-1))...(d1)defined by (for all i, (for all k,|{dik such that dik = 1}| = 1)) and (if 1 <= i < j <= p then 0 < di < dj) and (dp | dp-1 | ... | d1 = T). In other words,{di}is the ordered set of strings with a single1digit that makes up the stringTwhen|is applied.Let the result of the programme represent the following binary string:
((dp & S) << (p - 1))| ... | ((d2 & S) << 1) | (d1 & S)
Examples:
- 1111, 110 -> 11
- 1010, 110 -> 01
- 1010, 10110 -> 01
- 1101010111, 11111000 -> 01010
Input and Output:
- The two arguments may be taken in any way
- The two arguments need not be binary strings. They can also be integers which represent binary strings.
- Answers which do not take input representing binary strings of arbitrary length are permitted.
Winning: Shortest code wins.
Clarifications:
- If your output gives a bit string, order of bits is not important. Simply state the order in your answer. As stated before, the output of your programme need only represent the bits required.
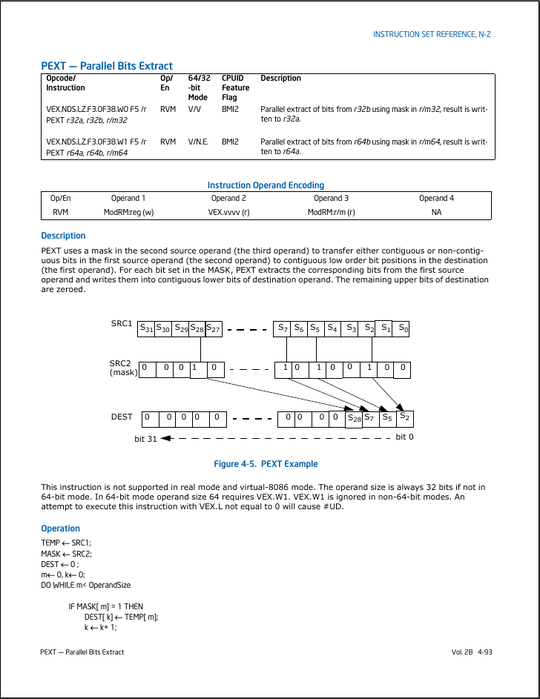
related on SO: Mask and aggregate bits
– Bergi – 2017-08-25T03:38:48.0701What's your objective winning criterion, i.e. how do you determine who wins? Shortest code, or something else? – Doorknob – 2014-09-01T12:19:07.400
I assumed that shortest code was the default criterion. I will add this to the post. – justinpc – 2014-09-01T12:50:52.393
Is there a maximum number of bits in each binary string? For example, can we assume that both inputs will be less than 100 characters long? – Doorknob – 2014-09-01T12:52:53.393
@Doorknob "Answers which do not take input representing binary strings of arbitrary length are permitted." ? – Martin Ender – 2014-09-01T12:55:17.863
As per the formal definition, there is no maximum input size. As per the third criterion of the Input and Output section, reasonable limits on input size may be imposed by the programmer, such as using only 32bit or 64bit input. – justinpc – 2014-09-01T12:56:12.950
1Your clarification allows reversed output. I assume it also allows reversed input? – John Dvorak – 2014-09-01T13:51:58.640
1Yes, if the input involves bit strings. – justinpc – 2014-09-01T14:05:58.033
Would you, could you, change the subscripting to use <sub></sub>? It won't work in backticks, but I think it would improve readability considerably. – Scott Leadley – 2014-09-01T14:21:57.010
In the first step of "Formal Definition:", I think
n>=0should ben>0to disallow(x_0)(x_1). – Scott Leadley – 2014-09-01T14:22:15.857Regarding subscripts: I would rather not take what is in backticks outside of backticks. On
n>=: I don't see what you mean. Could you please explain? – justinpc – 2014-09-01T14:41:36.227You could use something like
<code>x<sub>0</sub></code>; I'll edit the post when I get home. – Doorknob – 2014-09-01T17:55:02.193And the reward for the first sensible edit description in this question goes to... @MartinBüttner (thank you!) – John Dvorak – 2014-09-01T18:23:48.783
This really left itself open to exploitation of standard loopholes. That's why I downvoted. – Isiah Meadows – 2014-09-02T03:49:04.550
Let's just say that there was absolutely nothing prohibiting people from using specializes functions. Also, it was poorly defined enough that I lost interest rather quickly. It isn't a very clear specification (the ES6 specification is easier than this, and it's a full WIP language specification, with a lot of new features including module support, which is really complex). – Isiah Meadows – 2014-09-02T05:58:37.370