18
6
Let's say you have some text, and you want it to send it to your friend, but you don't want anyone else to read it. That probably means you want to encrypt it so that only you and your friend can read it. But, there is a problem: you and your friend forgot to agree on an encryption method, so if you send them a message, they won't be able to decrypt it!
After thinking about this for a while, you decide to just send your friend the code to encrypt your message along with the message. Your friend is very smart, so they can probably figure out how to decrypt the message by studying the encryption method.
Of course, since other people might be reading the message, you want to choose an encryption scheme that makes it as hard as possible to crack (figure out the decryption scheme).
Cops' Task
In this challenge, Cops will play the role of the writer: you will design an encryption scheme that converts strings to strings. However, this encryption scheme must be bijective, meaning that no two strings must map to another string, and every string can be mapped to by an input. It must take only one input—the string to be encoded.
You will then post some code that performs the encryption, and a single message encrypted with the scheme detailed by your code.
Since you are paying by the byte to send messages, your score will be the length of your code plus the length of the ciphertext. If your answer is cracked, you will have a score of infinity.
After one week, you may reveal the text and mark your answer as Safe. Safe answers are those that cannot be cracked.
Robbers' Task
Robbers will play either as the friend of the writer or the malicious middle man (there is no material difference, but you can role-play as either if it makes it more fun to do so). They will take the encryption schemes and the ciphertext and attempt to figure out the encrypted message. Once they figure out the encrypted message, they will post it in a comment. (There will not be a separate robbers' thread for this question.)
The winner will be the robber with the most cracks.
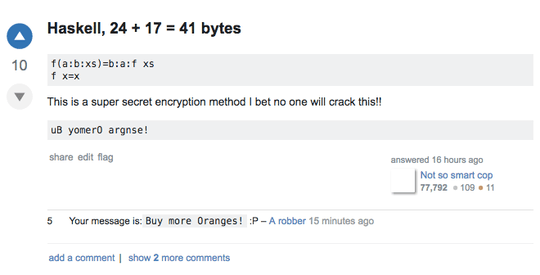
Here is an example of what a cracked solution might look like:
If the encoding is bijective, what are the domain and codomain? – Leaky Nun – 2017-07-19T18:21:35.453
The strings with which characters? – Leaky Nun – 2017-07-19T18:22:49.430
1@WheatWizard Which 256? You mean 256 bytes not characters right? – Erik the Outgolfer – 2017-07-19T18:34:06.907
7What's to stop somebody from using a cryptographically secure function? – Tutleman – 2017-07-19T18:49:45.120
Related challenge: All your bijective base are belong to us
– Ilmari Karonen – 2017-07-19T19:26:55.9072On who is the burden of proving bijectivity: the cop or potential robbers? I.e., if it is unknown if a function is bijective, what happens? – Stephen – 2017-07-19T19:28:27.480
@WheatWizard "I don't know of any function that is cryptographically secure when the key is given" without this you'd be practically left with no security. Practically all security rely on the fact that it is still secure when you know the algorithm. Look up RSA encryption. – Leaky Nun – 2017-07-19T19:39:19.520
@WheatWizard How is RSA not bijective? – Leaky Nun – 2017-07-19T19:51:03.050
@WheatWizard with one key there is only one encryption. – Leaky Nun – 2017-07-19T20:16:29.317
@WheatWizard I didn't use padding in my implementation. – Leaky Nun – 2017-07-19T20:33:18.130
So the trick here is, write a program in Malbolge. – KSmarts – 2017-07-20T15:04:17.393